Saturday, April 22, 2017
History of search engines
History of search engines
In the early days of Internet development, its users were a privileged minority and the amount of available information was relatively small. Access was mainly restricted to employees of various universities and laboratories who used it to access scientific information. In those days, the problem of finding information on the Internet was not nearly as critical as it is now.
Site directories were one of the first methods used to facilitate access to information resources on the network. Links to these resources were grouped by topic. Yahoo was the first project of this kind opened in April 1994. As the number of sites in the Yahoo directory inexorably increased, the developers of Yahoo made the directory searchable. Of course, it was not a search engine in its true form because searching was limited to those resources who’s listings were put into the directory. It did not actively seek out resources and the concept of seo was yet to arrive.
Such link directories have been used extensively in the past, but nowadays they have lost much of their popularity. The reason is simple – even modern directories with lots of resources only provide information on a tiny fraction of the Internet. For example, the largest directory on the network is currently DMOZ (or Open Directory Project). It contains information on about five million resources. Compare this with the Google search engine database containing more than eight billion documents.
The WebCrawler project started in 1994 and was the first full-featured search engine. The Lycos and AltaVista search engines appeared in 1995 and for many years Alta Vista was the major player in this field.
In 1997 Sergey Brin and Larry Page created Google as a research project at Stanford University. Google is now the most popular search engine in the world.
Currently, there are three leading international search engines – Google, Yahoo and MSN Search. They each have their own databases and search algorithms. Many other search engines use results originating from these three major search engines and the same seo expertise can be applied to all of them. For example, the AOL search engine (search.aol.com) uses the Google database while AltaVista, Lycos and AllTheWeb all use the Yahoo database.
Available link for download
Tuesday, April 18, 2017
How can I capture a video of my screen in fedora
How can I capture a video of my screen in fedora
Use VLC Player
How to install vlc?How to make a screencast using Vlc?
from a terminalsu -c yum -y install vlc

Select OPEN MEDIA
Select CAPTURE DEVICE tab
Change capture mode to DESKTOP
Change Options to 25 f/s
Choose CONVERT option instead of play option
In the Convert window add the destination file via the BROWSE
button then name the file TEST.MPG (VLC does require the extension so the file becomes TEST.MPG rather than just TEST)
Change the PROFILE to VIDEO - H.264 + AAC (TS)
Click the setting button and change the VIDEO CODEC options to:
BITRATE 1200kb/s
FRAME RATE 25.00 fps
Click SAVE
Choose the DEINTERLACE option
Click START
Available link for download
Sunday, April 9, 2017
Hackers reveals Secret of iphone 4s Siri Can Control Your Car via Voice Command !
Hackers reveals Secret of iphone 4s Siri Can Control Your Car via Voice Command !
Available link for download
Friday, April 7, 2017
Hacking The Internet Of Things Or Superenigmatix When Your Home Appliances Turn Against You
Hacking The Internet Of Things Or Superenigmatix When Your Home Appliances Turn Against You

Before I jump into the articles:
What is The Internet of Things? (IoT)
This article at Wikipedia will get you started:
https://en.wikipedia.org/wiki/Internet_of_Things
Here are a couple prescient articles about the inherent security problems of The Internet of Things. The first is from the Tips4Tech Blog from May 28, 2013:
Internet of Things? More Like the Internet of Attack Vectors
…And so now, we add the “Internet of Things” to the equation which will also be using Internet protocols. Companies and organizations that never had to deal with security issues will now have to think about ways to keep inbound and outbound data safe for all devices. Those of us who are security professionals have the tools and know the rules to keep most of the bad stuff out. But what happens when there is no oversight? Anybody will be able to get into the game of the “Internet of Things.” Most network devices have the ability to be secured, but who says that the vendors of this new world will know what to do?The second was written for the MIT Technology Review last August:
More Connected Homes, More Problems
They might offer convenience or potential cost savings, but Internet-connected home appliances may also create security risks.
- By Rachel Metz on August 13, 2013
…As we connect more and more devices to the Internet, everything from the thermostat to the toilet to the front door itself may create a potential new opening for electronic intruders. As with computers, there are ways to protect these devices from outsiders, but Crowley and Bryan’s experiences indicate that, for now at least, this isn’t always a primary concern for companies in a rush to sell this equipment. Making devices more secure can add time to product development....
Security researchers fear that the risks presented by these new types of gadgets are especially concerning. If hackers can exploit a weakness in a single type of Internet-connected home appliance or system—such as an Internet-connected door lock—they may be able to harm thousands of people at once. “It might be some effort to get this kind of scenario, but if breaking into one server means you get to ransack 100, 1,000, 10,000 people’s homes, that’s definitely worth it, and that’s where the real danger lies,” Crowley says.Then 2014 hits, and the freaky fun news begins!
Your home has been botted.

Security firm Proofpoint has uncovered a cyberattack that involved the hacking of “smart” home appliances connected to the Internet. Hackers broke into more than 100,000 gadgets -- including TVs, multimedia centers, routers, and at least one fridge – and used the appliances to send out more than 750,000 malicious emails between December 23 and January 6....
Perhaps worse: In “many cases,” the smart devices weren’t difficult to hack, according to Proofpoint. Instead, the appliances either were not set up correctly, or they used default passwords that were easy to find on public networks.Incorrectly setup home devices? Thats nothing new! I believe Ive written here previously about my hacking into a neighbors router to change their radio band setting to my leaching benefit! Once, I even had an IT professional argue with me that password encryption protecting of his home router was not important. He learned otherwise.
Proofpoint Uncovers Internet of Things (IoT) Cyberattack
More than 750,000 Phishing and SPAM emails Launched from "Thingbots" Including Televisions, Fridge
As the number of such connected devices is expected to grow to more than four times the number of connected computers in the next few years according to media reports, proof of an IoT-based attack has significant security implications for device owners and Enterprise targets....What astounds me is that the operating systems, memory and CPUs on these devices are powerful enough to even BE botted! Is this embedded system OVERKILL? I think so.
Cyber criminals intent on stealing individual identities and infiltrating enterprise IT systems have found a target-rich environment in these poorly protected internet connected devices that may be more attractive and easier to infect and control than PC, laptops, or tablets.This is SERIOUS Version 1.0 Syndrome. Oh dear!
The attack that Proofpoint observed and profiled occurred between December 23, 2013 and January 6, 2014, and featured waves of malicious email, typically sent in bursts of 100,000, three times per day, targeting Enterprises and individuals worldwide. More than 25 percent of the volume was sent by things that were not conventional laptops, desktop computers or mobile devices; instead, the emails were sent by everyday consumer gadgets such as compromised home-networking routers, connected multi-media centers, televisions and at least one refrigerator....
"Many of these devices are poorly protected at best and consumers have virtually no way to detect or fix infections when they do occur. Enterprises may find distributed attacks increasing as more and more of these devices come on-line and attackers find additional ways to exploit them." . . . .
"The Internet of Things holds great promise for enabling control of all of the gadgets that we use on a daily basis. It also holds great promise for cybercriminals who can use our homes routers, televisions, refrigerators and other Internet-connected devices to launch large and distributed attacks", said Michael Osterman, principal analyst at Osterman Research. "Internet-enabled devices represent an enormous threat because they are easy to penetrate, consumers have little incentive to make them more secure, the rapidly growing number of devices can send malicious content almost undetected, few vendors are taking steps to protect against this threat, and the existing security model simply wont work to solve the problem."Oh great! No user incentive to make their Internet of Things more secure. Bot wranglers must be in ecstasy!
My first question when a friend (Hi Nick!) pointed out this news was What manufacturers make these insecure refrigerators?!
I have yet to find a decent list of smart (or perhaps stupid is more descriptive) appliance manufacturers. But it turns out that companies involved in the technology end of The Internet of Things are vast! Here is one ongoing list:
Internet of Things – Big List of Companies, Products, Devices and Software by Sector
Obviously, this is going to be an enormous subject in 2014, if not for years. Keep an eye out as the botnet of The Internet of Things develops.

The Philosophy
Ludditism
n.I know there is some argument about the actual facts of the Luddite movement and its meaning. But Luddite has nonetheless become the single most popular term for anyone motivated to turn their back on technological progress. I also know that using this term is a great way to raise the hair of any tyrannical technologist.
1. Any of a group of British workers who between 1811 and 1816 rioted and destroyed laborsaving textile machinery in the belief that such machinery would diminish employment.
2. One who opposes technical or technological change.
There are a number of sci-fi books using the theme of Ludditism. One I recently read was The Difference Engine by none other than William Gibson and Bruce Sterling.
With the catastrophe of ones router, oven, refrigerator, door lock, home entertainment, lighting and alarm systems all conspiring against you, can you imagine the lash-back from certain users whod rather just go back to the old ways? I certainly can!
The Song
From back when I was a kid, one of my favorite music mavens is Bill Nelson, formerly of the group BeBop Deluxe. In 1978 he wrote the first of his hyperactive future-paranoia albums entitled Drastic Plastic. My favorite song from the album, the one that best summarized his artistic theme at the time, was Superenigmatix (Lethal Appliances for the Home with Everything). Here, for your reading pleasure, are the lyrics. Note their significance to the current plight of The Internet of Things:
Superenigmatix, theres one hiding in the attic,Here is a link to the song itself, as uploaded to YouTube. I cant guaranteed that such things are allowed to last at YouTube. But for the moment:
And its getting all ecstatic cause it goes on automatic,
When the lights go out.
Theres one in the TV and its waiting there to please me,
And Ive got to take it easy cause I know that it can see me,
When the lights go out.
Inside, outside, watching me both night and day.
Sometimes I wish I could make it go away.
Sometimes when Im dreaming, I awake to find Im screaming,
Cause theyve taken all the meaning from the book that I was reading,
When the lights went out.
I know it seems outspoken but Id love to see them broken,
No more orders, no more slogans, no more keeping my eyes open,
When the lights go out.
Inside, outside, watching me both night and day.
Sometimes I wish I could make them go away.
Superenigmatix, always amateur dramatic,
And theyre trying to get me at it,
But I think Im going to kick them in!
http://www.youtube.com/watch?v=kXHGPbRb7NU
Enjoy (!) And Share,
:-Derek

Available link for download
Saturday, April 1, 2017
Google Summer of Code 2013
Google Summer of Code 2013
Google Summer of Code has been a great success throughout this years and its 2013 and Google Summer of Code (GSOC) 2013 is now being officially announced. GSOC has been an annual tradition by Google and open source project to collaborate and enabling students to learn something from the open source community via their mentors and also contributes back to the project by working on certain things or features that hopefully will be implemented on that project. Many open source project has received this benefits.
If you are a students and would like to join GSOC 2013, head to the website and check their timeline and also FAQs
Available link for download
Monday, March 27, 2017
Hidden On the trail of the Ancients PC Games Full Version Downloads Free PC Game
Hidden On the trail of the Ancients PC Games Full Version Downloads Free PC Game


Immersed into dark and unexplored ancient woods a group of expeditioners goes deep in search of an old, almost forgotten legend, the “Legend of the Ancients”. But not everything goes as planned as the place keeps a never revealed horrifying secret.
You play the game as Thomas Farrell, a young anthropologist and one of the expeditioners behind the search of evidence about the Legend of the Ancients.
Thomas traveled to Buenos Aires, where an old colleague of his uncle Eneko seems to have found an important trail to the Ancients.
His investigations start in an old boarding house and soon he will realize that there is something hidden beyond the legend.
Hidden is a high-res, atmospheric first person horror point n’ click adventure game with focus on story, puzzles and exploration. The storyline is split into two games: On the trail of the Ancients and The Untold.
Key Features
Rich and mature Story, strengthened with docs, books, audio records and visual elements along the adventure.
Classic Point n’ click gameplay.
Intriguing and immersive detailed high-res locations set in the 30s.
Story oriented puzzles.
Original and gripping score for each location.
In-Game detailed collectibles to enhance to the story.
Horror fiction inspired by writers such as Algernon Blackwood and H. P. Lovecraft.
 Tags:- Hidden On the trail of the Ancients Syndicate Gold Edition Preload, Hidden On the trail of the Ancients Syndicate Gold Edition Preload torrent, Hidden On the trail of the Ancients Syndicate Gold Edition Preload download, Hidden On the trail of the Ancients Syndicate Gold Edition Preload uplay, Hidden On the trail of the Ancients Syndicate Gold Edition, Hidden On the trail of the Ancients Syndicate Gold Edition torrent, Hidden On the trail of the Ancients Syndicate Gold Edition crack, Hidden On the trail of the Ancients Syndicate Gold Edition preload, Hidden On the trail of the Ancients Syndicate Gold Edition preload torrent, Hidden On the trail of the Ancients Syndicate Gold Edition uplay preload, Hidden On the trail of the Ancients Syndicate Gold Edition unlocker, Hidden On the trail of the Ancients Syndicate Gold Edition crack only,
Tags:- Hidden On the trail of the Ancients Syndicate Gold Edition Preload, Hidden On the trail of the Ancients Syndicate Gold Edition Preload torrent, Hidden On the trail of the Ancients Syndicate Gold Edition Preload download, Hidden On the trail of the Ancients Syndicate Gold Edition Preload uplay, Hidden On the trail of the Ancients Syndicate Gold Edition, Hidden On the trail of the Ancients Syndicate Gold Edition torrent, Hidden On the trail of the Ancients Syndicate Gold Edition crack, Hidden On the trail of the Ancients Syndicate Gold Edition preload, Hidden On the trail of the Ancients Syndicate Gold Edition preload torrent, Hidden On the trail of the Ancients Syndicate Gold Edition uplay preload, Hidden On the trail of the Ancients Syndicate Gold Edition unlocker, Hidden On the trail of the Ancients Syndicate Gold Edition crack only, 




- OS: Windows XP / Vista / 7 / 8
- Processor: Intel Core 2 Duo 2.0 GHz, AMD Athlon X2 2.0 GHz
- Memory: 2 GB RAM
- Graphics: Intel HD 3000 (dual channel RAM recommended), GeForce 8600 GT, Radeon HD 3650 with 512MB video memory
- Hard Drive: 4 GB available space
- OS: Windows XP / Vista / 7 / 8
- Processor: Intel Core 2 Duo 2.0 GHz, AMD Athlon X2 2.0 GHz
- Memory: 3 GB RAM
- Graphics: Intel HD 3000 (dual channel RAM recommended), GeForce 8600 GT, Radeon HD 3650 with 512MB video memory
- Hard Drive: 4 GB available space


| Click On any link n Wait 5 seconds then Skip Ads | ||
| Download Torrent Client | U torrent | |
| Download Server 1 | Download Torrent | |
| Download Server 2 | Download Torrent | |
Available link for download
Friday, March 24, 2017
Help Us Stop the Updates to Rule 41 EFF Calls for a Day of Action on June 21st
Help Us Stop the Updates to Rule 41 EFF Calls for a Day of Action on June 21st

"U.S. government agents want to use an obscure procedure to radically expand their use of hacking techniques. We need to stop them.
"The change to Rule 41 would make it easier for U.S. government agents to break into our computers, take data, and use hacking techniques.
"The rule change especially impacts people using privacy-protective technologies, including Tor and VPNs.
"The United States Congress never approved this expansion of the FBI’s powers. But now, Congress is our last chance to stop the change from taking effect."
Please reject the changes to Rule 41 of the Federal Rules of Criminal Procedure by passing the Stopping Mass Hacking Act (S.2952, H.R.5321). These amendments would lead to a vast expansion of government hacking, a largely unregulated law enforcement technique that makes us all less secure.
"We’ve written a detailed explanation of the changes to Rule 41, which explains why this update will result in a dramatic increase in government hacking. Here’s an overview of some of the main reasons we are concerned:
"Government agents hacking into computers more frequently is a recipe for disaster. Law enforcement will increase their exploitation of security vulnerabilities in common software products, meaning vulnerabilities that could affect millions will be left open instead of patched.
"Law enforcement will forum shop, finding government-friendly magistrate judges to sign off on warrants with a loose connection to the judicial district.
"Law enforcement will pressure judges to sign off on remote searches of thousands of computers with a single warrant—a direct violation of the Fourth Amendment and a pattern we’re already seeing.
"This rule change especially impacts people using privacy protective technologies like Tor or VPNs, which is why we’re asking privacy tools to join us in standing up for users on June 21."


Available link for download
Monday, March 20, 2017
How to Increase the Internal Memory of Android Devices
How to Increase the Internal Memory of Android Devices
First your android device has to be rooted,There is absolutely no way you can increase the size of your phone’s internal storage but you can allocate some part of your memory card for your phone to install applications to.
Cautionary Disclaimer: I am not Responsible if your brick you device or something happens to
your Device.
Guide to using Link2SD on your Android smartphone.
3) A Computer
Follow the Procedure below:
There is no need to wipe your memory card when going through this process, just ensure you have at least 0.5GB to 1.0GB of free space to make it worthwhile. You also do not need to use a microSD card adaptor as the process below creates the partition whilst the phone is connected to your PC.
a) Connect your Memory card to the PC via USB Card reader and then launch MiniTool. You should see the details pop up under ‘Disk 2?. In your case it may show as Removable Disk.









a) Open the Link2SD app on your phone. You should be greeted with the following menu, check the FAT32 option and click OK.

You will then see the Superuser Request, Select ‘Allow’.

Once you see the following message, restart your phone. The app should now be ready to use.

b) To make sure everything is installed correctly. Click the Menu button and go to ‘Storage Info’. This will show you the internal memory and your two partitions on the memory card. In our case, you can see that the second partition has 1GB free.

c) Now you need to move the apps of your choice to the memory card. Click the Menu button and press ‘Multi-select’.

Choose which apps you want to move by clicking the tick box next to the app. System apps are greyed out and cannot be selected. Link2SD can only move apps that are already on the internal memory. If you have apps already on your SD card, you will need to move them back to the internal memory before you can link them with Link2SD.

If you want to move all of your apps, pressing the menu button will bring up another menu allowing you to do this.

d) Once you have chosen which apps you want to move, you then need to hit the menu button and press ‘Actions’, which will bring up the following menu. Press ‘Create Link’.

Leave all three check boxes ticked and press OK. Link2SD will now do its work and move/link the selected apps to your memory card.

Once finished, you should see that the apps you have moved have ‘Linked -> SD Card’ in red font in the Link2SD app list. Reboot your phone.

e) Congratulations your phone is now using Link2SD! You should now go to Settings by pressing the menu button and configure how you would like Link2SD to work. The main decision here is whether you want to Auto Link newly installed apps to the memory card. Given that you’ve gone through the hassle of installing Link2SD we suggest you enable Auto Link and make worrying about your internal memory a thing of the past.
Please Leave a Comment
Available link for download
Tuesday, February 28, 2017
Honai of Android How to Root Galaxy S4 I9500 on Android 4 4 2 KitKa
Honai of Android How to Root Galaxy S4 I9500 on Android 4 4 2 KitKa
Honai of Android: How to Root Galaxy S4 I9500 on Android 4.4.2 KitKa...: Samsung has recently released the Android 4.4.2 KitKat update with firmware build number I9500XXUFNB3 for the Exynos 5 octa-core variant ...
Menerima Service Komputer, Laptop. Notebook, Printer Upgrade, Hardware, Software, Instalisasi, dll. Antar Jemput/ Panggilan Hubungi kami DATUN di: Telp : (+6221)70183469 Hp : +628881128512 E-mail : sadatun.ajri@gmail.com sadatun.ajri@yahoo.coms sadatun.ajri@telkomproperty.co.id
Available link for download
Monday, February 27, 2017
How to fix error 5200 of Canon IP2770
How to fix error 5200 of Canon IP2770
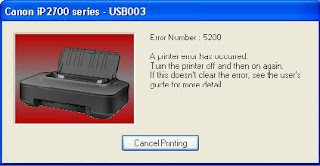
Available link for download
Tuesday, February 21, 2017
How to Make a Gingerbread House to Outlast Even the Sweetest of Sweet Tooths CraftStylish
How to Make a Gingerbread House to Outlast Even the Sweetest of Sweet Tooths CraftStylish
How to Make a Gingerbread House to Outlast Even the Sweetest of Sweet Tooths - CraftStylish
Posted using ShareThis
Available link for download
Monday, February 20, 2017
How to Edit the Contents of an ISO Disk Image in Ubuntu
How to Edit the Contents of an ISO Disk Image in Ubuntu
As many knows already, you dont need any other application other than an archive manager if all you want is to view the contents (+ even changing the contents) of an ISO disk image file. But if you want more than that, such as mounting the content or changing it without loosing the boot-able core files (if any) then you will have to use a dedicate tool nonetheless.
And when concerning the contents of an ISO file that holds an operating system for instance then yes, you can still use an archive manager to add/delete files from it ... but if you do so, them most of the time after doing your changes, youll have an un-bootable ISO disk image.
The reason is simple. An archive manager is simply an archive manager thus (most of the time) it wont be able to edit the content without destroying the "Boot Record" portion that includes all the information needed for making it boot-able.
In that case, if you happened to use Ubuntu ;-), then theres an excellent Utility called "ISO Master" that lets you do exactly that.
 |
| Welcome to the master of the "ISO", kiyahooooooooooooo! ;) |
*. Add/Edit/Rename and delete the contents of an ISO file.
*. Only supports the ISO disk image extension (although you can read other extensions such as NRG and MDF, more later).

*. Has the ability to view certain types of files such as HTML and Text related ones.
*. Extract the contents (since a disk image is a sort of an archive).
*. Save/Delete or manually change the Boot-record according to your own preferences... are its main features.

You can install IsoMaster in Ubuntu 11.04 Natty Narwhal, 11.10, 10.10 and 10.04 by using the below command in your Terminal window.
sudo apt-get install isomasterRemember if you want to view some of the contents of the disk image file, say a configuration file or a Text file for instance. Then if you use a desktop other than Xfce, then make sure to go to its "Options" window and change the "viewer" command to "gedit" if you use Gnome classic desktop or with whatever your preferred editors name.
 |
| By default it uses the Editor "mousepad" (Xfces text editor). But I replaced with my own... |
Another thing, ISO Master also supports reading ISO, NRG and MDF files as well. But it can only save files the .iso format only.
Anyhow, if you want to create a bootable ISO disk image (CD/DVD, etc) file using files in your HDD from scratch or modify the content of an existing disk image (without destroying its core-properties such as above mentioned boot-entries) then ISO Master is certainly one of the best without a doubt. Its also free and even supports MS Windows too (Windows version is not free though :/).
Available link for download
Thursday, February 16, 2017
How could you know the total number of SMS Text Messages you got
How could you know the total number of SMS Text Messages you got

One of the pre-installed application on Samsung galaxy phones is SOCIAL HUB.

It includes all the messages you had on your SMS and Email. From this you will see the total number of messages youve been received and sent including those that were failed to be sent.
The number 0 in 0/268 indicates that there is no unread message(s) and
The number 268 indicates the total number of messages.
Available link for download
Tuesday, February 14, 2017
Hack Windows using winAUTOPWN 3 4 –Completing 4 years of windows hacking
Hack Windows using winAUTOPWN 3 4 –Completing 4 years of windows hacking
winAUTOPWN has been an old favourite to automate windows hacking and vulnerability testing. The project is the brainchild of Azim Poonawala of [C4]Closed Circuit Corporate Clandestine and saw its first release in 2009. Fast forward to 4 years; it has matured into a good exploitation framework with a plethora of options. As the Author states about it -
Autohack your targets - even if you have consumed and holding a bottle of ABSOLUT in one hand and absolute ease (winAUTOPWN) in the other.
In layman terms, winAUTOPWN is a unique exploit framework which helps in gaining shell access and pwning (aka exploiting vulnerabilities) to conduct Remote Command Execution, Remote File/Shell Upload, Remote File Inclusion and other Web-Application attacks. To add cherry on the top, it can also help in conducting multiple types of Denial of Service attacks on targets, furthermore, It can also be used to test effectiveness of IDS/IPS and other monitoring sensors/softwares.
You can -
- Download winAUTOPWN from here / mirror
- Read its documentation from here
Available link for download
Monday, February 6, 2017
Guns of Infinity 1 0 3 Cracked APK
Guns of Infinity 1 0 3 Cracked APK
Guns of Infinity 1.0.3 Cracked APK
Guns of Infinity 1.0.3 Cracked APK
Firearms of Infinity
As authority of a squadron of mounted force, what will you give up to win the war of black powder and enchantment? Come back to the front line as a man of his word officer of the Royal Tierran Army in this hotly anticipated spin-off of "Sabers of Infinity."
Will you become a close acquaintence with, sell out, or sentiment the nobles, mavericks, and spies of this epic world? Will you keep your men alive, or penance them to your own particular ravenousness in an offer for influence and wealth? Will you battle for influence, wealth, love, or superbness?
Assume the part of a courageous legend, or a self-serving fraud.
Use tricky, drive, or sheer boasting to battle the Antari powers.
Prepare and bore your men for accomplishment on the front line.
Support your crew fiscally, or abandon them to battle off penury alone.
Battle, interest, and sentiment anticipate in "Firearms of Infinity!"
How to introduce?
Direct Download Link
Download Link Userscloud
Download Link revclouds
Available link for download
Wednesday, February 1, 2017
Ho Ho Ho and lots of Snow
Ho Ho Ho and lots of Snow



Well, unless youre a troll in a dungeon somewhere, you know it snowed here in Loveland this week--mostly sideways snow. This recent storm really reminded me of Wyoming. Fortunately though, we had nowhere we had to be....
There are thousands of pix on the web of the Blizzard of 2006, but heres my small contribution anyway....
Available link for download
